Information Security
We Advance IT Security
The Information Security research group of the InIT addresses issues related to the development of secure software systems (Software Security) and the study of cyber attacks and defense (Cyber Attacks and Defense). Among other things, we address questions such as:
- How can functionality be implemented in a secure manner?
- How can the level of automation in security testing be increased?
- How can publicly available information be used to detect threats?
- What security mechanisms are needed for future communication networks?
- What is the role of security awareness and how can it be improved?
The knowledge gained from applied research and development is also incorporated into our continuing education Offerings:
and our Bachelor- (Introduction to Computer and Communication Security, IT Security, Software and System Security 1, Software and System Security 2) and Master modules (IT-Security).
The Information Security research group is part of the ZHAW Cybersecurity Community. As such, it is also a member of the Swiss Support Center for Cybersecurity (sscc).
Software Security
The topic of Software Security covers the modeling, realization, and analysis of software systems that fulfill a number of security requirements.
Our research concentrates on the analysis by means of (automated) security testing and the development of novel security mechanisms and protocols. Thereby, the quality, efficiency and reproducibility of the tests as well as the protection of domain-specific functionality are the main focus.
A current project on this topic:
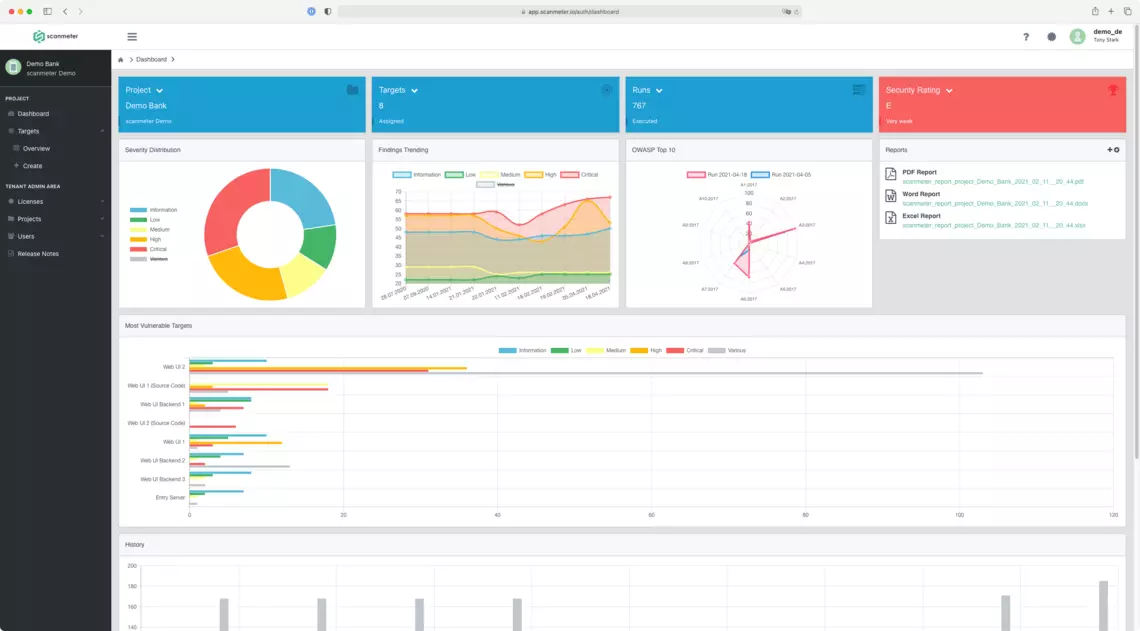
In this R&D project, scanmeter - a service for the automated security analysis of IT systems - is being extended by three innovative components. This will significantly increase the level of automation and test coverage, significantly improve customer benefits, and expand the fields of applications. Specifically, the following should be achieved in the project: (1) scanmeter will support automated security testing of APIs, significantly increasing the range of applications (e.g., to modern web applications, mobile apps and Internet of Things (IoT) devices); (2) scanmeter will be able to detect all types of access control vulnerabilities in web applications, providing comprehensive support for this critical vulnerability type; and (3) scanmeter will support arbitrary authentication processes in web applications and APIs, enabling full test automation with respect to authentication as well.
The project is carried out in cooperation between InIT and scanmeter GmbH.
Cyber Attacks and Defense
The topic Cyber Attack and Defense covers the modeling, analysis, and realization of cyber attacks and of defensive measures.
We research and develop solutions to combat current threats more effectively. In particular, we focus on threats related to the introduction and use of new technologies (e.g. 5G/6G networks), the improvement of the defense posture (e.g. using OSINT), machine learning and the human factor.
A current project on this topic:
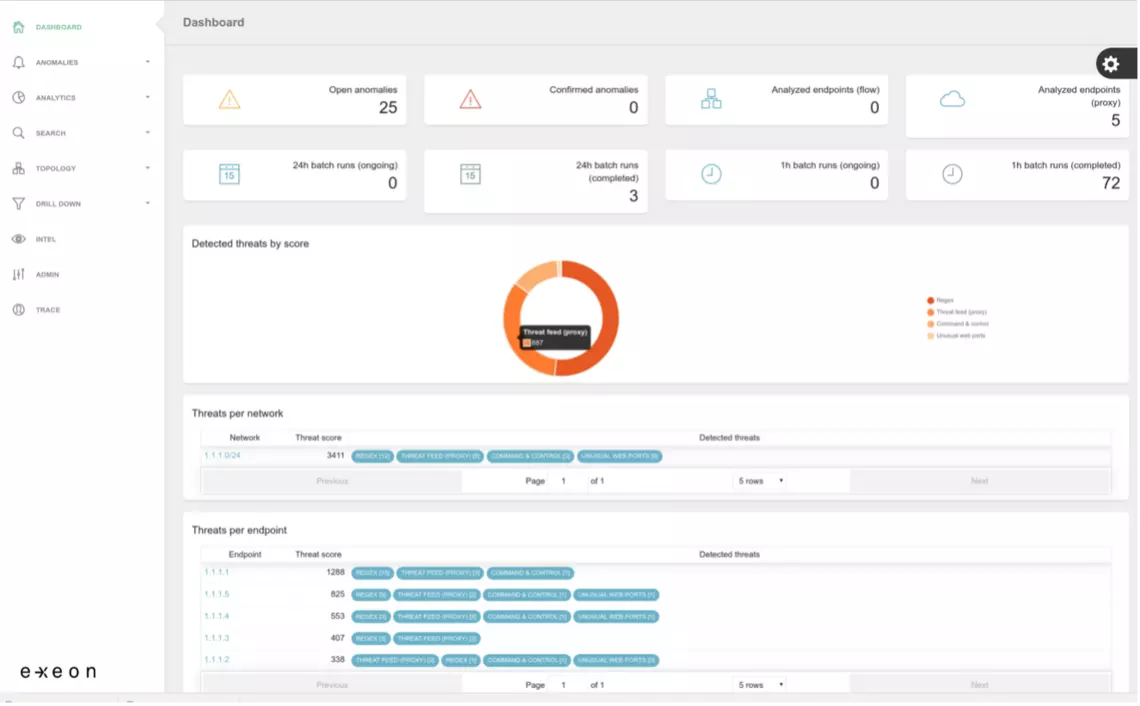
This project extends Exeon Analytics' ExeonTrace product with HostDetective Next Generation (HD.ng), a tool to identify and mitigate Web-related data breaches. HD.ng implements a novel active and passive Web server assessment method to determine the type, purpose and risk score of a Web server. This project builds on the results of the HostDetective project.
Continuing Education
Our CAS Applied IT Security (German only) offers the opportunity to computer scientists, practitioners and career changers the opportunity to build and enhance their foundation in IT Security, one of the most important growth markets in IT. Participants will be introducted into security architecture and management, cryptology and network security as well as software and systems security. They will be given the opportunity to apply their new skills in extensive and practice oriented labs.
-
Dynamic Security Analysis of Android Pre-installed Apps
The project aims at enhancing security testing methodologies for Android pre-installed applications. It encompasses empirically evaluation of hindering factors associated with dynamic analysis of pre-installed apps on the Android emulator. To be more precise, the feasibility of rehosting Android pre-installed apps, ...
-
Net-Zero self-adaptive activation of distributed self-resilient augmented services (NATWORK)
The ambition of the EU NATWORK project funded by Horizon Europe - 6G SNS (2024-2026) is to set the foundations and deploy the very first economically realistic, energy efficient, and viable bio-inspired AI-based 6G cybersecurity and resilience framework for intelligent networking and services, taking a holistic ...
-
HD.ng++ Automated Web Server Classification
The HD.ng++ project creates a system to support an analyst in a Security Operations Center (SOC). The developed system provides meta-information on domains and IP addresses to assist SOC-Analysts by the investigation of potentially malicious domains or IP addresses.
-
Sutter, Thomas; Lapagna, Kevin; Berlich, Peter; Rennhard, Marc; Germann, Fabio; et al.,
2021.
Web content signing with service workers.
ZHAW Zürcher Hochschule für Angewandte Wissenschaften.
Available from: https://doi.org/10.21256/zhaw-22514
-
Porambage, Pawani; Gür, Gürkan; Moya Osorio, Diana Pamela; Liyanage, Madhusanka; Gurtov, Andrei; Ylianttila, Mika,
2021.
The roadmap to 6G security and privacy.
IEEE Open Journal of the Communications Society.
2, pp. 1094-1122.
Available from: https://doi.org/10.1109/OJCOMS.2021.3078081
-
Kushnir, Malte; Favre, Olivier; Rennhard, Marc; Esposito, Damiano; Zahnd, Valentin,
2021.
In:
Proceedings of the 7th International Conference on Information Systems Security and Privacy.
ICISSP 2021, online, 11-13 February 2021.
SciTePress.
pp. 204-216.
Available from: https://doi.org/10.5220/0010300102040216
-
Gür, Gürkan; Porambage, Pawani; Liyanage, Madhusanka,
2020.
Convergence of ICN and MEC for 5G : opportunities and challenges.
IEEE Communications Standards Magazine.
4(4), pp. 64-71.
Available from: https://doi.org/10.1109/MCOMSTD.011.1900045
-
Gür, Gürkan,
2020.
Expansive networks : exploiting spectrum sharing for capacity boost and 6G vision.
Journal of Communications and Networks.
22(6), pp. 444-454.
Available from: https://doi.org/10.23919/JCN.2020.000037